1. Technology life cycle analysis

FIG. 1 Growth rate v trend of safety prevention technology with a 5-year cycle
V trend formula description: technology growth rate = A /A, where A is the number of invention patent applications (or the number of approvals) in the current year;A represents the cumulative number of invention patent applications (or the cumulative number of approvals) traced back five years.After several years of continuous calculation, the v value increases, indicating that the technology is in bud or growth stage.
As can be seen from Figure 1, before 2009, security prevention technology was in the stage of technical introduction, while from 2009 to 2011, the technology was in the growth stage, and after 2011, the technology gradually matured.In this technology field, according to its citation frequency and the number of patent applications of the same family, it is concluded that there are many key patents.The distribution of important patent literature in this field has a long time span, from the 1980s to this century, there has been a continuous distribution of important patents, and the security technology patents mainly appeared after 2008.
The analysis shows that the security prevention technology has been in its infancy for a long time, but its development is relatively slow due to the limitation of the technology. With the development of wireless communication technology and Internet technology, the security prevention technology has also entered the stage of rapid development.Since 2009, the technology has made breakthroughs.
2. Analysis of principal applicants
In the field of security and prevention technology, the top 10 patent applicants in the world include SAMSUNG, LG, Gree Electric Appliances,Inc. Of Zhuhai, State Grid Corporation of China, SEOUL COMMTECH CO LTD, Haier Group, Fangchenggang LvHuayuan Agriculture and Forestry Technology CO LTD, Sun Yat-sen University, Shenzhen Jieluo Information Technology CO LTD, etc.
As can be seen from Figure 2, the number of patent applications of SAMSUNG and LG is still in the forefront.The stability of the patent of Chengdu Kechuang City Technology Co., LTD., which ranks the top, remains to be verified.The company was registered and established in March 2015, and its business scope includes software development, computer system integration, sales of computer hardware and software, etc. In 2015, it applied for a number of smart home related patents, but the authorization rate was not ideal. Up to now, 27% of the patent applications have been invalid.
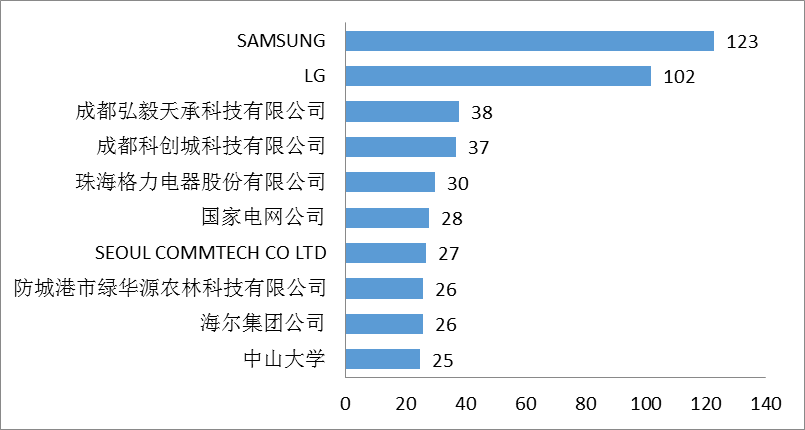
FIG. 2 Main applicant for security technology
3. Analysis of important patents in the sub-fields of security technology
The security prevention technology mainly focuses on home security, and the security prevention technology mainly consists of access control system and home security monitoring system. The following will specifically analyze the important patents of these two technologies.
The earlier patent (US5086385A) was filed by Custom Command System in 1992.It discloses a home automation system, which uses video surveillance camera to monitor around the house, and outputs the video to the surveillance panel through the camera to realize the security monitoring of the house.The safety system functions of the system include the alarm function of fire and other accidents, and the monitoring of the family equipment and the family safety condition is relatively perfect.This patent and its kindred patent have been cited for 1452 times in the world, which was obviously innovative and advanced at that time and belonged to the basic patent.
With the development of network technology, how to monitor home security conveniently has become a hot research topic.The patent application submitted by China United Communications in 2006 (CN1988489A) (as shown in Figure 3) is entitled "A System and method for intelligent furniture monitoring".After the patent by remote terminal access to the Internet, send home web server user account and password, the navigation terminal unit to the user account and password forwarded to information exchange server authentication, the remote terminal ID and set up information channel between the home gateway ID, realize the remote control all electrical equipment in the home, and make full use of CDMA 1 x 153.6 KBPS characteristics of high-speed data transmission in the home has a real-time transmission image alarm when abnormal situation, monitoring situation in the home at any time, even when away from home, also know the situation in the home, and achieve the visual, audible, controllable and the effect of active alarms.After the patent was published, it was cited by a large number of patents, with citation frequency up to 52 times.After the patent was published, it was immediately purchased by China Telecom group, which further indicates that remote monitoring and security technology has become a hot topic of major companies' attention.
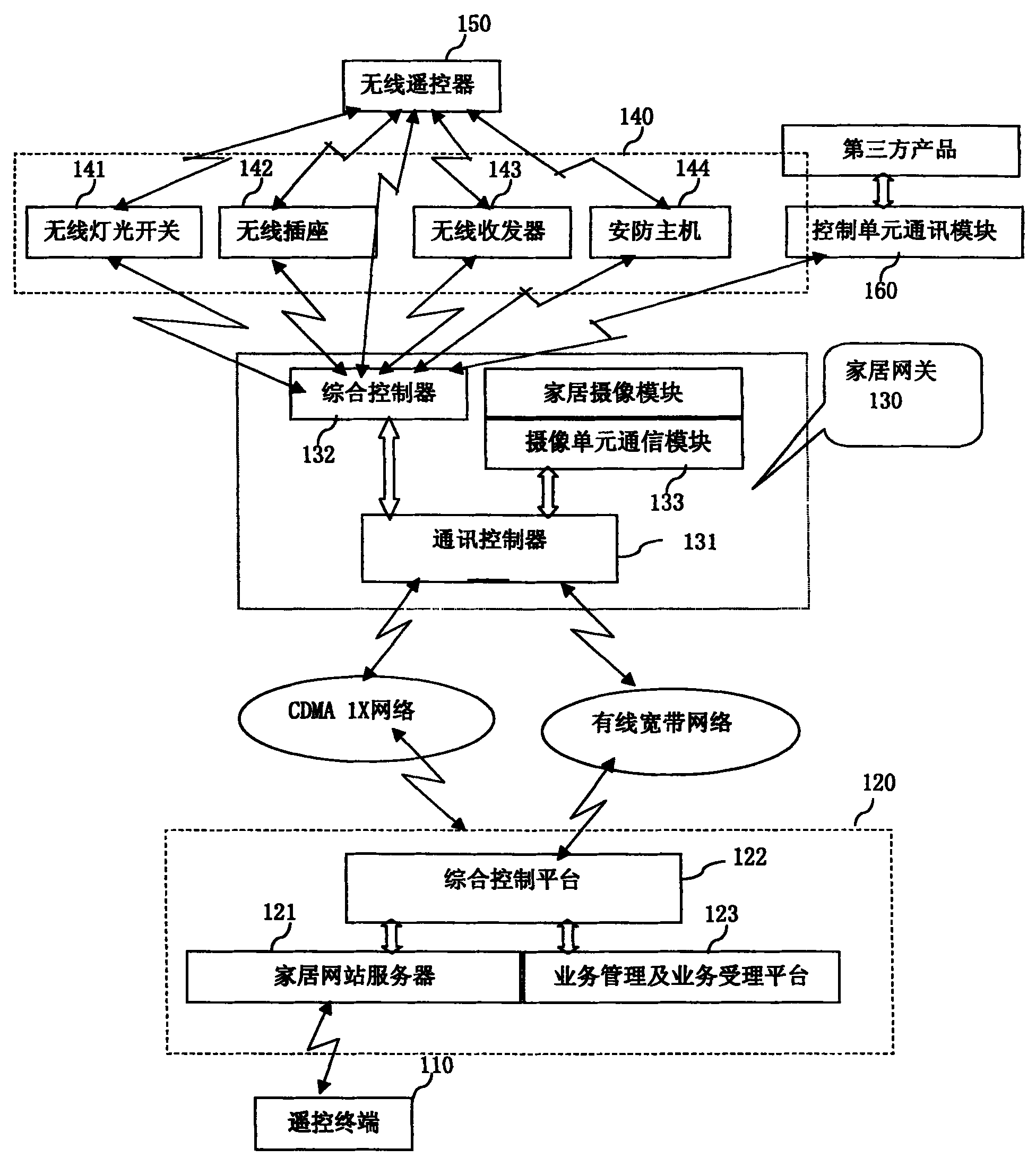
FIG. 3 System and method of intelligent furniture monitoring
However, with the development of wireless transmission technology and the appearance of smart phones, remote monitoring and audio-visual can no longer meet people's needs, and security prevention technology with high intelligence and low energy consumption has become people's pursuit direction.The patent (CN102882752A) applied by Tianjin Guanghong Technology Co., Ltd. in 2012 describes a smart home system and control method based on the Internet of Things and Android system.Through zigbee, blueTooth, wifi, 3G and other wireless transmission methods, the home monitoring environment is transmitted to the mobile phone client in real time, enabling users to view and manage the home living environment anytime and anywhere.At the same time, the anti-theft system can realize the automatic deployment and removal of anti-theft in the automatic control mode, and realize the intellectualization of home security technology.2014, Google company applied for more than about handheld terminal access server's patent, the patent inpadoc kin as high as 131 in the whole world, patent layout in the United States, Canada, South Korea, Japan, China and other countries, in the case of intelligent home monitoring technology is increasingly perfect, Google company from basic technology research and development, the patent layout, looking for breakthrough.
In the field of access control system, the earliest identification technology is contact identification, that is, the use of magnetic stripe card, bar code card and other identification information, such as in the 1870s of the United States patent (US3116380A, US3274352A, US3434130A), etc., have revealed the use of contact magnetic card for identification and opening of the door lock technical solution.The patent of related technology only appeared gradually after 1996 in China.As the contact identification method is prone to the failure of the magnetic card or loose insertion of the card, and with the emergence of radio frequency technology, Bluetooth, wifi and other wireless transmission technologies, the application of non-contact identification technology is born.For example, the patent (US20030179073A, WO2008041016, CN101211427A, CN2859666Y) and other devices are installed in the identification card through non-contact identification method to carry out identity information identification.
At the same time, with the development of fingerprint, face and other biometric recognition technologies, the number of patent applications applying fingerprint, face and other recognition methods to access control system technology also increases.For example, Qingdao University applied for a home intelligent access control system based on face recognition and 3G communication in 2010 (CN101980305), and Shenzhen Anxing Decoration Design Engineering Co., Ltd. applied for an intelligent access control system based on multiple identification method in 2014 (CN203799428U).In order to facilitate the entry of visitors, it is more common to install a digital keyboard at the entrance of the building and communicate with the members of the house by means of voice phone or video phone to realize remote control of the door lock.For example, shenzhen Borang Intelligent Technology Co., Ltd. applied for the smart home wireless optional plug-in access control system (CN203386253) in 2013, and Nanjing Zhijie Iot Applied for a building intercom system based on wireless communication (CN205121664) in 2015.With the emergence of intelligent terminal devices, remote door opening can be realized by installing related applications on intelligent terminals, adopting NFC technology and using intelligent terminals to exchange identities with access control system.Such as the 2010 Zhang Hongxin application of network intelligent security doors (CN102074056A), tangshan and the ford intelligent control application based on android intelligent security door (CN104265135A), 2015, shenyang wisdom remit wantong technology application and monitoring system for a door of guard against theft device (CN105279872A), three gorges university in 2016 applications based on cell phone video surveillance and security door and use method and chengdu didi control technology for a intelligent village entrance guard intercom system based on Internet of things (CN205647806U) are releasedAs a client, mobile phone uses mobile Internet terminal to realize remote video monitoring and remote opening.
At present, in the field of security prevention technology, the docking of security prevention technology with mobile phones and other smart terminals has become a hot spot of research and development.In the research and development process, enterprises pay more attention to the use of functions, but relatively ignore the underlying technical support.In patent layout aspects, therefore, enterprises on the one hand, can be perfect on the function of the intelligent monitoring aspect in the family, on the other hand, should also pay attention to the underlying information transmission technology, information processing speed and response speed of research and development, in the process of security technology research and development, can from the core technology of enterprise, to strengthen the core technology of surrounding patent layout at the same time, strengthen the competitiveness of the enterprise.
Note:This article is the original patent analysis article of ZYIP Research Institute. Reprinting of this article must be approved by the right owner, with the source and author information attached. Reprinting is prohibited without the permission of the author.